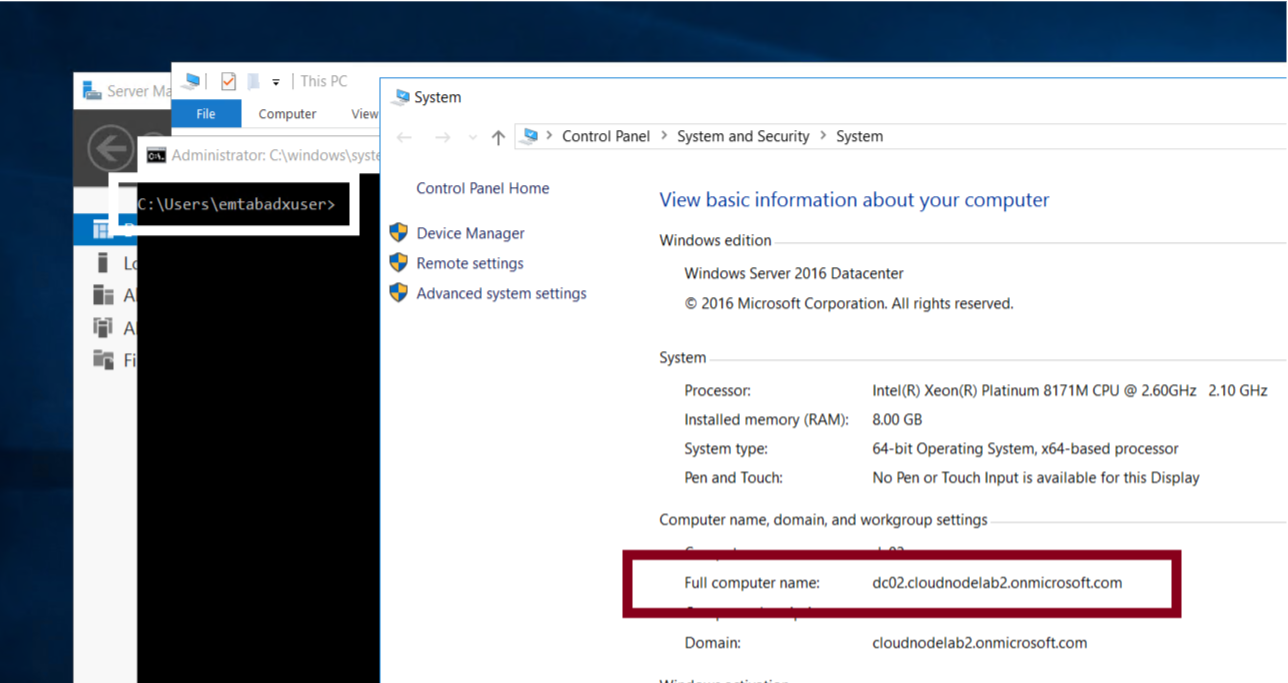
This post is a good continuation of the post we had earlier about creating an Azure ADDS instance. You can check out the post on the following link.
The trust doesn't use Azure AD connect to achieve its goal, it passes through a Site-to-Site VPN between Azure and the on-premise environment.
For this article, I'm going to use a domain controller deployed in a VNet that is separate from the VNet used by my Azure ADDS to achieve the same result that we would for connecting to the on-premise environment. VNet peering is the method of choice in this scenario. If you don't know how to setup VNet peering, please check out one of my previous articles here.
To get started, I will set up a new domain using an Azure quick start template, as shown below.
Next, we set up our new domain by inserting the values that fit our environment.
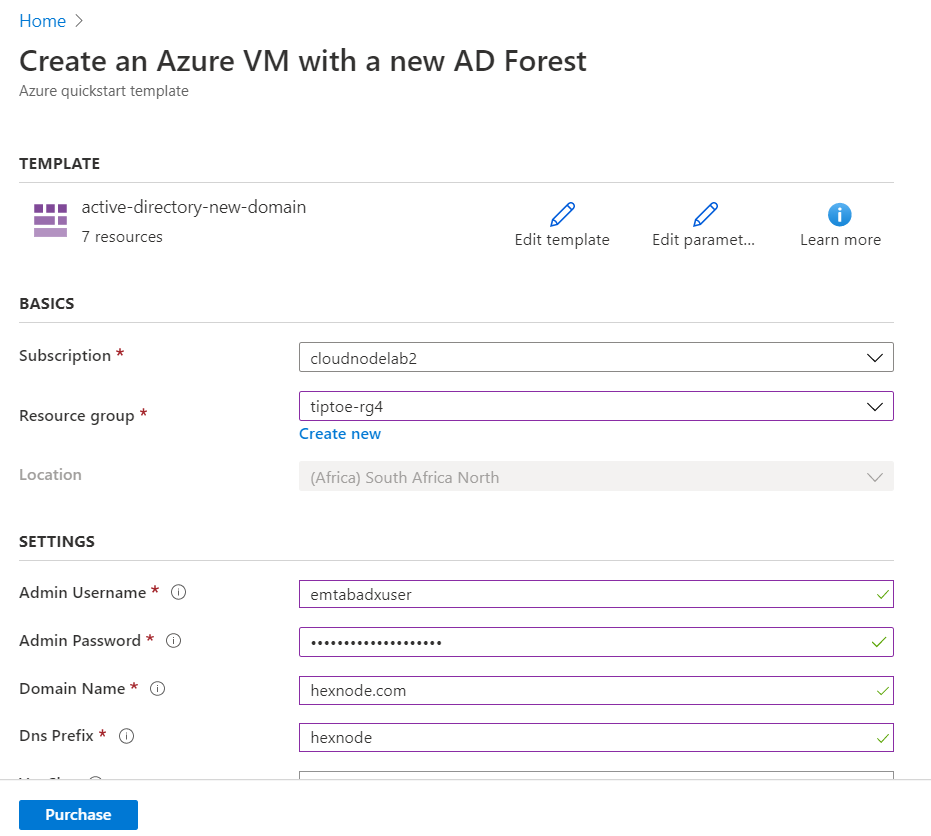
The template is also available in the GitHub repo below.
After deploying the new Active Directory domain in a separate VNet (Remember VNet peering helps us emulate the Site-to-Site VPN setup), we will go ahead to attempt the two objectives below:
- Create a one-way inbound forest trust in an on-premises ADDS environment.
- Create a one-way outbound forest trust in Azure ADDS.
To proceed, we need to set up the DNS forwarders to point to our Azure ADDS by configuring them in the DNS Manager of our on-premises server, as shown below.
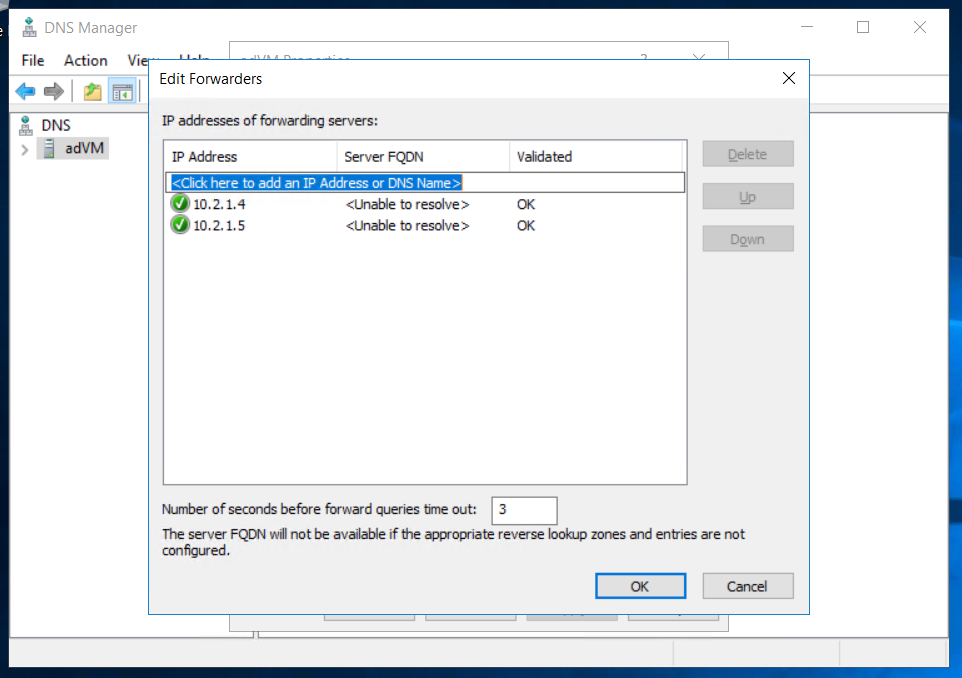
The two IP Addresses above represent the private addresses of our Azure ADDS instance.
The next thing is to configure is Active Directory Domains and Trusts. To set this up, right-click on our Active Directory Domains and Trusts in the console, select properties, select trusts, and click on creating a new trust.
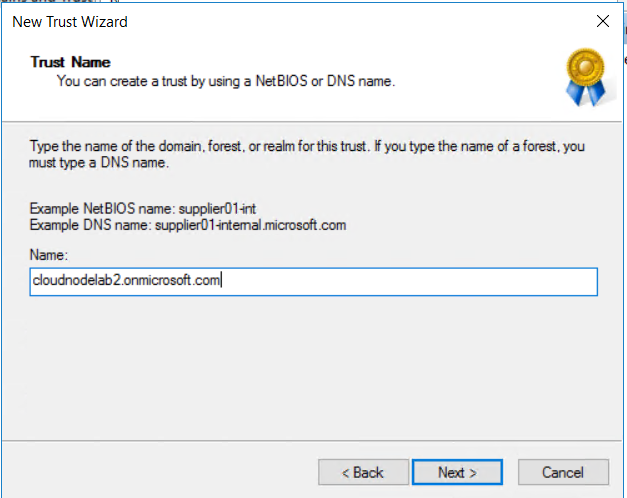
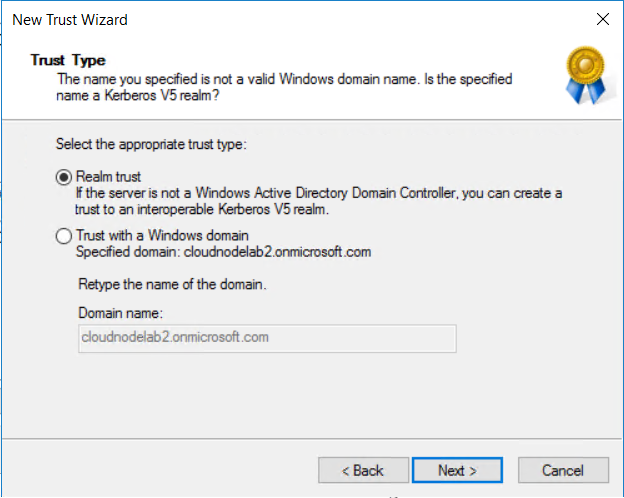
Next, insert the name of the domain you want to create the new trust.
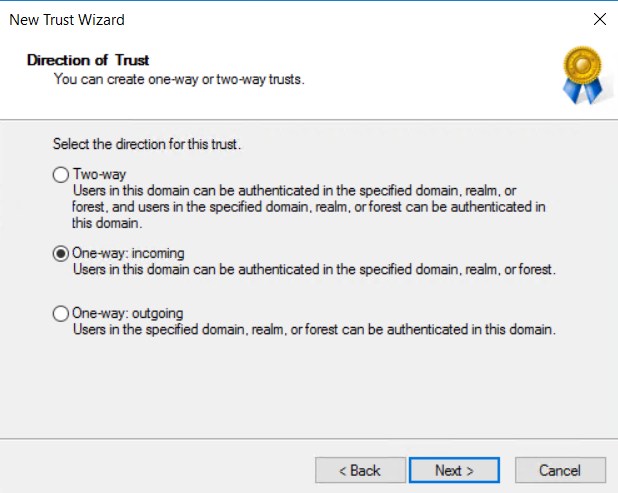
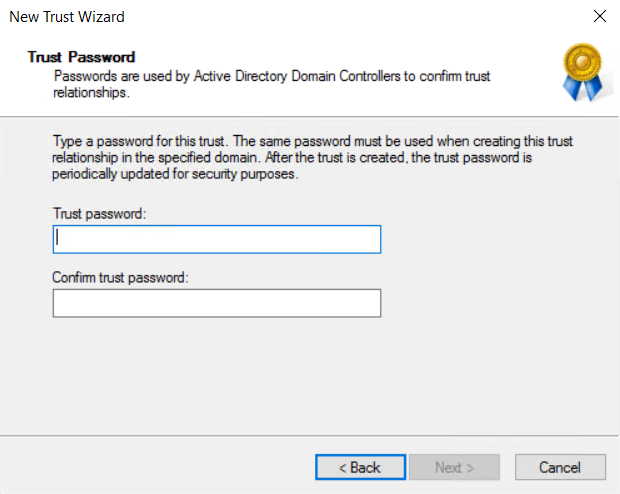
Next, create a one-way incoming trust from our trusted domain and create the password, then finish creating your trust on the on-premise side.
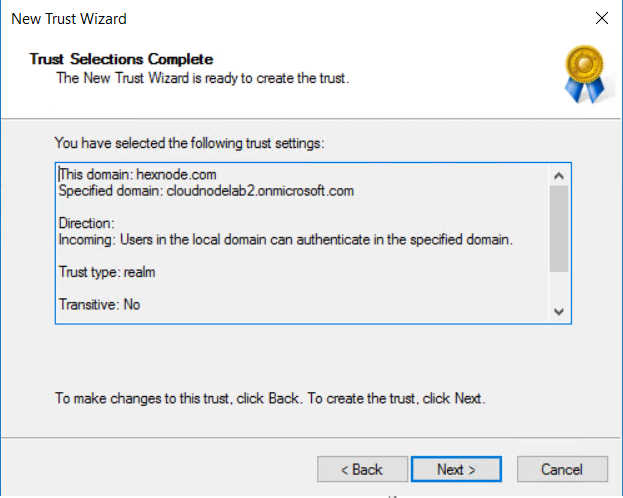
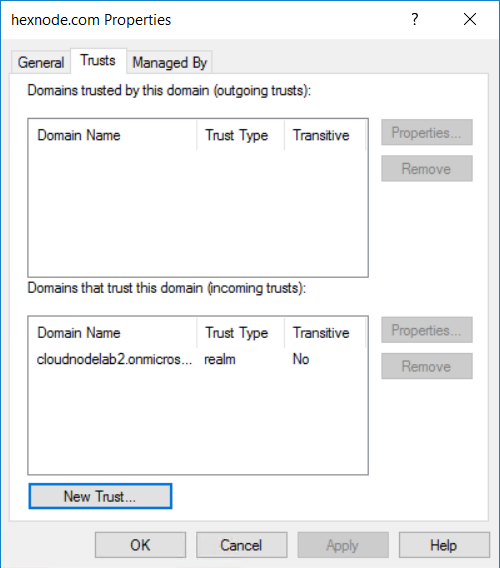
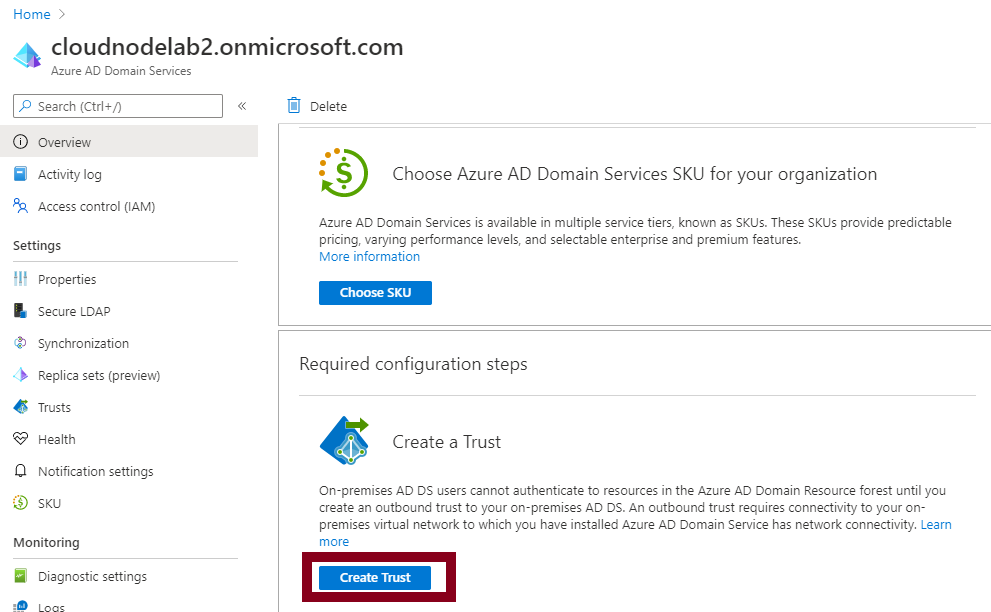
Next, head to your Azure ADDS and create a new trust.
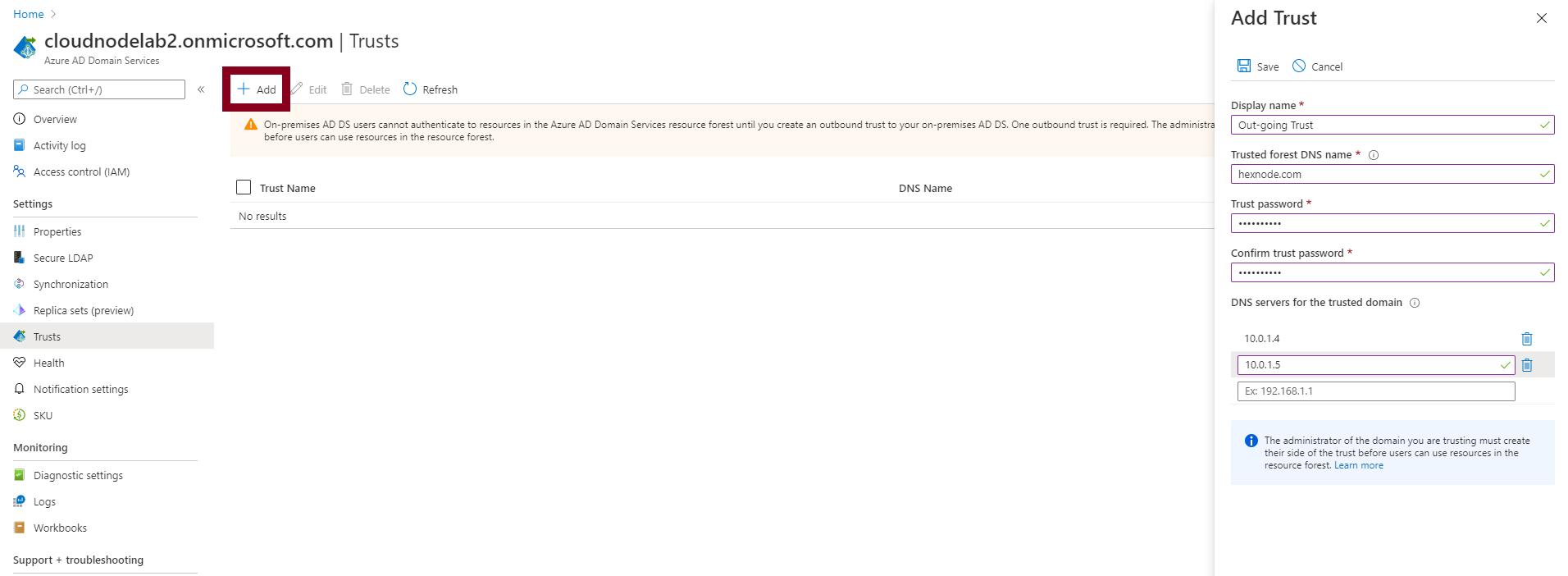
We then define our out-going trust with the forest domain, trust password, and the DNS servers for our on-premises domain and save the new trust.
To confirm that our trust relationship is okay, I will remote into one of the domain controllers joined to the Azure ADDS domain using the user credentials of one domain user of my local domain (on-premises domain).